Here at nClouds, our clients often ask for our help to connect their on-premises infrastructure with the AWS infrastructure when they want to:
- Sync their on-premises data center with Amazon Elastic Compute Cloud (Amazon EC2), so that they can:
- Add more compute capacity to their network.
- Launch additional web servers.
- Move their corporate applications to the cloud.
- Communicate efficiently and securely:
- Between on-premises and AWS – reducing the need for users to continually log in to a Virtual Private Network (VPN) connection.
- Between various remote corporate sites – using the AWS infrastructure to avoid unnecessary exposure of their network to the Internet.
Sound familiar? If so, read on to learn how to set up an AWS Site-to-Site VPN between your on-premises network and an Amazon Virtual Private Cloud (Amazon VPC) network over the Internet.
At a high level, what you need to do is create an IPsec VPN connection between your VPC and your remote network: a virtual private gateway with two VPN endpoints (tunnels) on the AWS side and a customer gateway on the remote (customer) side.
Following is an example of how I created an AWS Site-to-Site VPN for one of our clients.
Customer Use Case
Our client, an innovative online healthcare provider, wanted to connect their on-premises network to the AWS infrastructure to enable them to:
- Connect to Amazon EC2 instances in the private subnet on AWS without having to configure additional VPN configurations.
- Provide local access to their application running on AWS.
Here is the architecture I created for the AWS Site-to-Site VPN, replicating an on-premises infrastructure on AWS using Amazon EC2 instances and replicating the VPN using Openswan (an IPsec implementation for Linux) to set up the request:
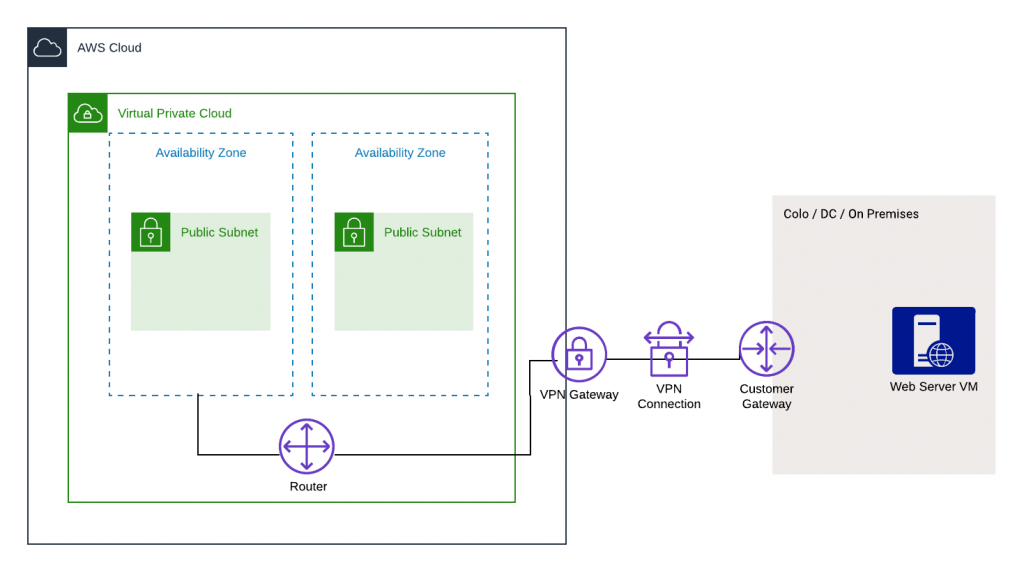
And, here are the nine steps I took to create this architecture:
- On the AWS side, since we were replicating both the AWS and client-side setup, I created two VPCs in different Regions, assigned different Classless Inter-Domain Routing (CIDR) ranges to each VPC, and set up an Amazon EC2 instance in each VPC.
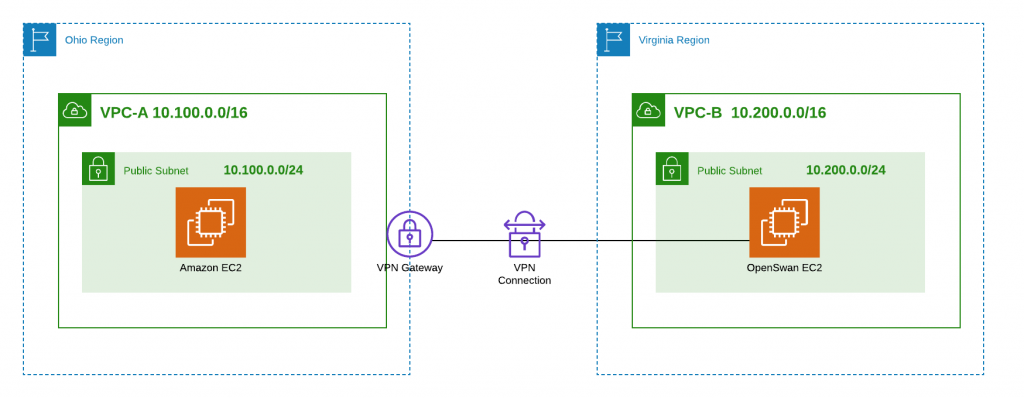
- Set up Openswan on the Amazon EC2 instance to replicate the client’s infrastructure that would be acting as a router.
- Created a virtual private gateway (the anchor on the AWS side of the VPN connection) and enabled route propagation on the route tables so that the tunnels created were added to the route table automatically.
- Set up the customer gateway (the anchor on the customer side of the VPN connection) by entering a valid name and giving the IP of the customer’s router (using Openswan to replicate the router).
- Created the AWS Site-to-Site VPN by selecting the previously created virtual private gateway and the customer gateway. I provided the customer CIDR range in this step.
- Once the AWS Site-to-Site tunnel was up, two tunnels were created for high availability in case one tunnel goes down.
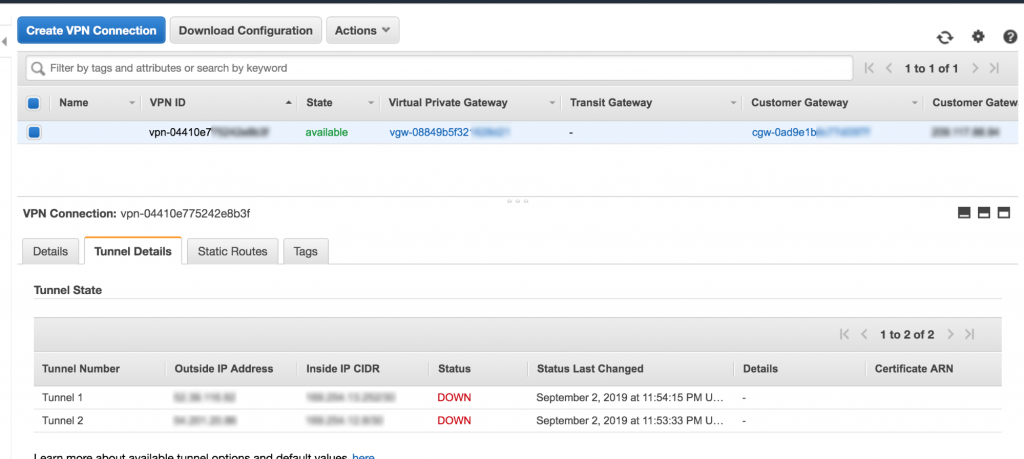
- Downloaded the client configuration from AWS and provided it to the client so they could set it up on their end. In this case, I used SSH (Secure Shell) to connect to the Amazon EC2 instance running Openswan and updated the configuration.
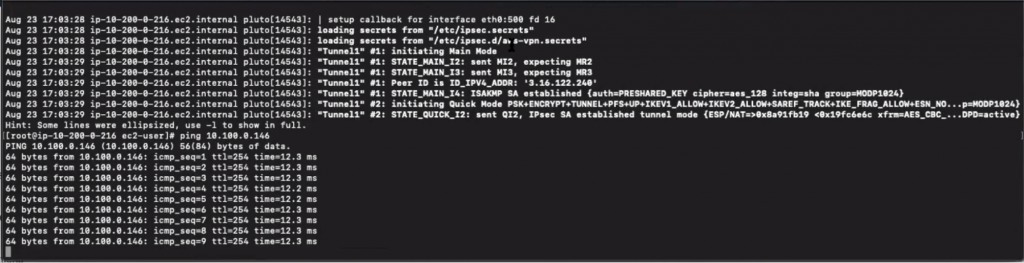
- Restarted Openswan. After a short while, the tunnels came online indicating that the Site-to-Site VPN was now functional.
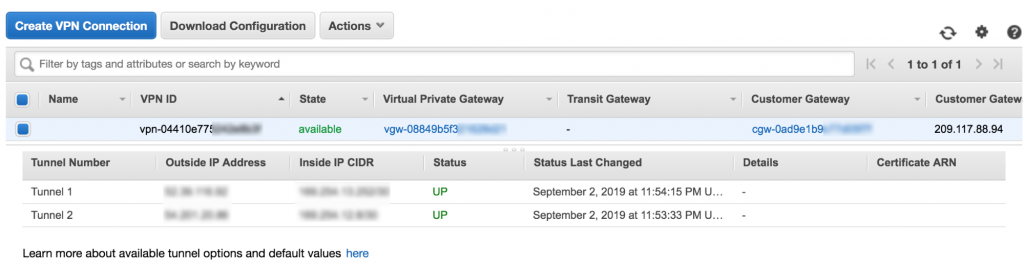 Beware of this “gotcha”: The tunnel needs to have consistent traffic flowing through the connection – the default timeout is 10 seconds – otherwise, the tunnel will go down. If your use case does not have this logic enabled, you can set up “keepalive” ping requests to flow steadily.
Beware of this “gotcha”: The tunnel needs to have consistent traffic flowing through the connection – the default timeout is 10 seconds – otherwise, the tunnel will go down. If your use case does not have this logic enabled, you can set up “keepalive” ping requests to flow steadily. - Pinged the Amazon EC2 instance set up in the other region from the instance running Openswan to confirm that the Amazon EC2 instance was reachable.
In conclusion:
By creating an AWS Site-to-Site VPN tunnel, you can:
- Access your on-premises environment without third-party tools.
- Enhance the reliability of your infrastructure.
- Gain greater control over your infrastructure by keeping some portion of it on-premises while running other operations on the AWS Cloud.
Need help to connect on-prem with AWS? The nClouds team is here to help with that and all your AWS infrastructure requirements.


