I’ve been working DevOps on cloud environments for a while now, and it’s almost always a given that you need a virtual private network (VPN) when you’re working in the cloud. For a time, OpenVPN was the go-to solution (possibly because people thought it was the only one), but after gaining more experience with VPNs, you realize there are just a few viable options — each with distinct pros and cons.
So when AWS came out with a VPN solution for AWS environments, I was pretty excited and wanted to know about its features, usage, pricing and everything else. But, at the initial launch, I have to say I was a little disappointed. The main two reasons for disappointment were a lack of SAML (Security Assertion Markup Language) authentication and that this VPN only worked on Mac and Windows (I use Linux daily, but there wasn’t Linux client support). However, as is the case with many AWS services, everything changed in just a few short months. Now there’s support for SAML and an AWS VPN Linux client, which I think are both good reasons to revisit this product.
A quick overview of the AWS VPN
The AWS VPN is an excellent alternative to OpenVPN and offers a lot of utility and flexibility when you use it with your SSO (single sign-on). AWS made this VPN service more useful with the addition of new authentication features. Now, you can use the AWS VPN with less of the hassle of managing a VPN for many different users — avoiding creating separate client endpoints and issuing separate certificates for every VPN user.
In this overview, I’ll show you how to leverage AWS VPN’s authentication features, including federated access through SAML and when you’re using the Linux desktop client. The AWS VPN offers support for several types of authentication, offering additional flexibility with controlling access. Initially, the only two ways to authenticate were by exchanging certificates and using active directory support.
SAML support streamlines the VPN experience for users and enables you to more easily control, grant, and revoke access as needed. By setting up your SSO to work with AWS VPN, you can connect and create as many profiles as you need for users while also simplifying the process of configuring and managing the VPN and access.
Setting up AWS VPN SSO authentication
This process works inside the AWS SSO console and requires some custom settings in addition to downloading a VPN client. Once you’ve set up your VPN profile, you can launch via a VPN application tile in your SSO console.
Create a custom SSO application
- Create an application in the AWS SSO console: Although AWS VPN is an AWS product, it doesn’t have a predefined application so you will need to create a custom application within SSO.
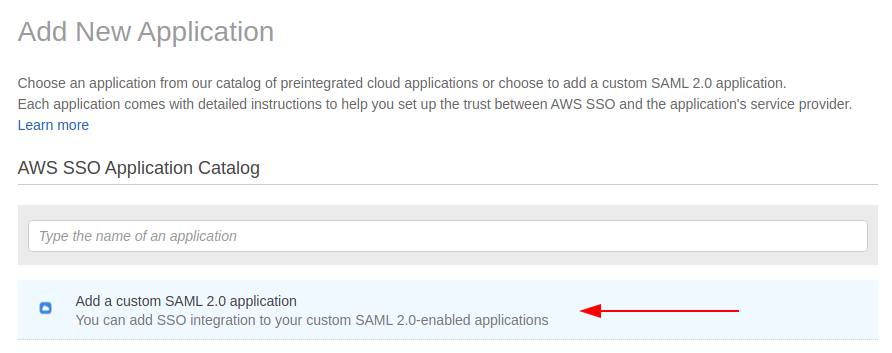
- Download the XML configuration file: After the download, you’re ready, and your application is configured.
Creating the VPN
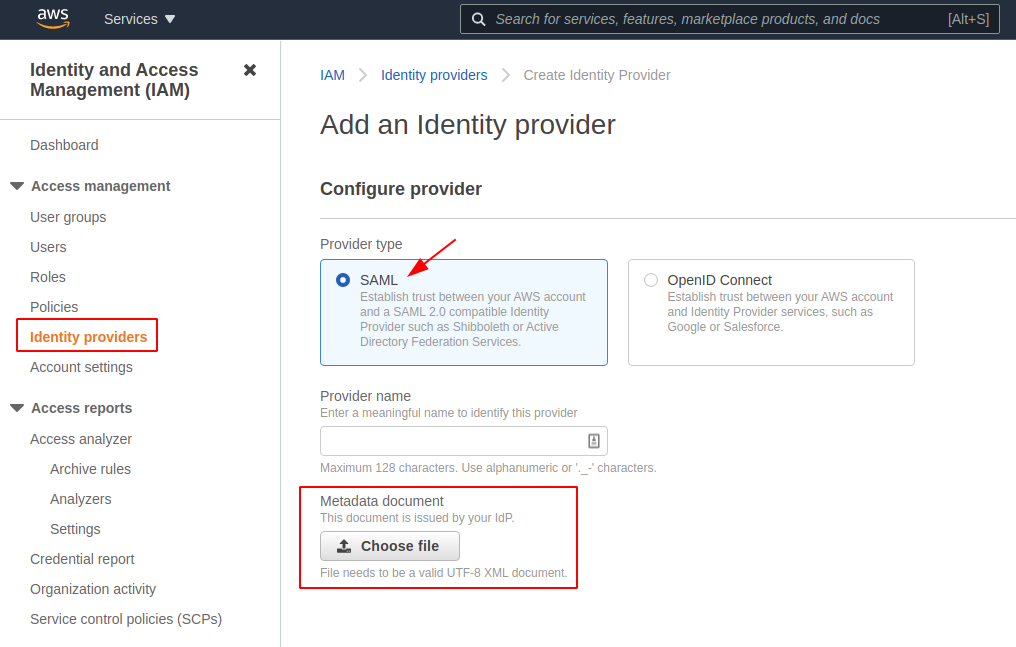
- Set up an IAM (Identity and Access Management) identity provider (IdP) entity: In the AWS Management Console, open the IAM Console and navigate to Identity Providers. Create an IdP, choosing SAML in the console. Choose any name for your identity provider and upload your metadata document (created by the identity management software your organization uses).
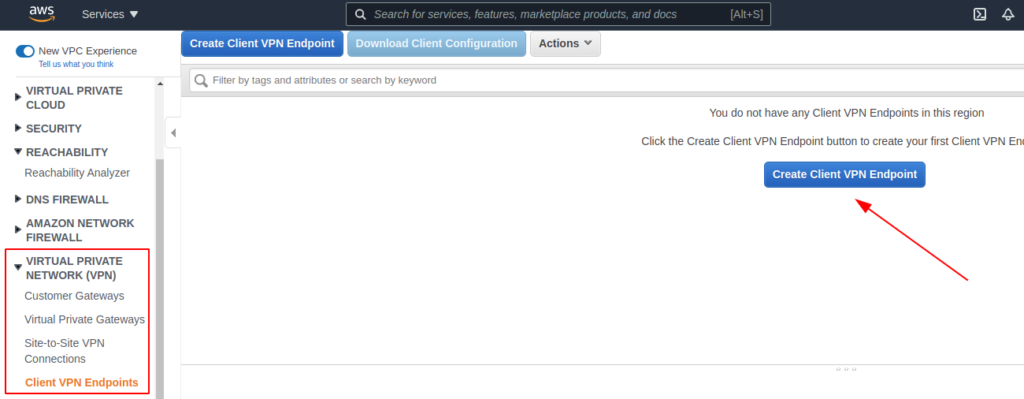
- Create Client VPN endpoints: A Client VPN endpoint must have at least one target network to enable clients to connect to it and establish a VPN connection. Within Create Client VPN Endpoint in the console, choose a name and description. Next, choose a specific IP address range that doesn’t overlap with the target network (subnet). Specify a certificate ARN (Amazon Resource Name).
- Establish Federated Authentication: Federated Authentication makes it easy to integrate AWS Client VPN user authentication and authorization with a centralized, SAML-based Identity Provider (IdP). Select Use user-based authentication and Federated Authentication to take advantage of the new authentication option for your VPN. You’ll choose a SAML provider and make optional decisions about connection logging and client connect handling — you can leave these last two empty. From there, after selecting the options you want, choose Create Client VPN Endpoint.
- Create Client VPN association to a target network: Associate a subnet to the Client VPN Endpoint.
- Set authorization: In the Authorization tab, choose Authorize Ingress. You can set up authorization rules permitting all users or specific access groups. (Remember, however, that the AWS SSO does not share information about which groups a user belongs to on the SAML exchange, so this limitation can prevent group restriction from working.)
- Set attribute mappings: In the SSO console, choose the VPN application you just created earlier and map the basic attributes you’ll need for signing on, such as username, email, ID, first name and last name. Working from the attribute list, map any attributes you need. Keep in mind that directory attributes need to be in the form ${dir:AttributeName}.
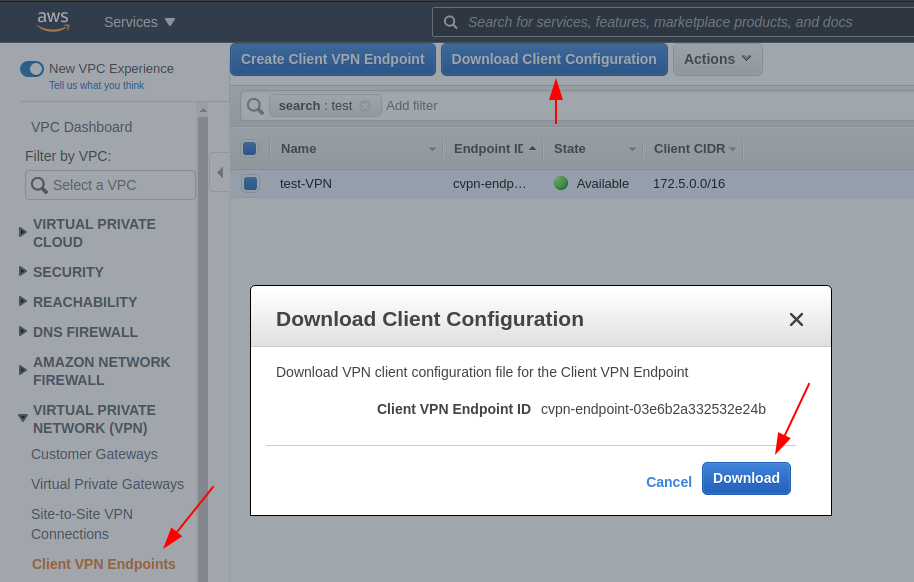
- Download the VPN client configuration file: You need this to connect to the VPN successfully. Windows, Mac, and Linux versions are available, with the Linux version now offering federated authentication.
Using AWS Client VPN
- Open AWS Client VPN: By clicking the File tab, you can select Manage Profiles.
- Create a profile: Add a new profile. You can create as many profiles as you need.
- Keep the Client VPN open and launch your application: From your SSO tiles, choose the VPN application you added to SSO and launch it. Be sure to keep your Client VPN open to connect.
If you have issues connecting, refresh and relaunch the application and client and try again. You will probably need to keep the client open and your AWS application active to use your VPN service.
AWS Client VPN desktop client for Linux
In June 2021, AWS released support for SAML-based federated authentication on the Linux desktop AWS Client VPN. This desktop client already supported certificate-based and Active Directory authentication and now offers more authentication flexibility.
With the scalability and flexibility of the AWS Client VPN service and application, there are a variety of use cases. Securely access your on-premises environment and scale remote access. Organizations undertaking a cloud migration, supporting a remote workforce, or looking for a fully managed VPN solution could benefit from trying the AWS VPN service.
Do you need help with your AWS infrastructure? Connect with the nClouds team — we can help free up your engineers for high-value, innovative projects to achieve your technical and business goals on AWS. Contact us.


