Since its inception in 2009, Chef has quickly become the go-to configuration management tool for developers and companies. While the tool is highly successful at streamlining the tasks of configuring and maintaining a company’s servers, handling sensitive data within Chef continues to be a bit of a challenge. For companies that are dealing with extremely sensitive content, especially healthcare providers that must be compliant with the Health Insurance Portability and Accountability Act (HIPAA), this suddenly becomes a much more urgent issue to solve. This is where Amazon Web Services (AWS) Key Management Service (KMS) comes in.
KMS is a managed service that makes it easy to encrypt and decrypt sensitive data, ensuring that systems facilitate HIPAA compliance while processing, managing, and storing protected health and patient information. Combined with other AWS services, KMS can be a powerful method to inject secure credentials into automated instances, while still helping you to protect the data you store.
Some Benefits of KMS
Fully Managed: One of the biggest benefits companies report about using KMS is the fact that it is fully managed. This allows you to be able to focus on the encryption of your applications instead of having to spend time and energy maintaining the tool. AWS handles the physical security, availability, and the hardware maintenance of the underlying infrastructure.
Centralized Key Management: KMS provides a centralized system of control of all of your encryption keys, allowing you to view all of the key usage in your entire organization in one location. It also helps you create, import, and rotate keys easily and efficiently.
Encryption for All Applications: Another huge benefit of KMS is that it makes it extremely simple to manage encryption keys that are stored by your applications, regardless of where they are stored. KMS provides a software development kit (SDK) to assist with the integration of encryption and key management into all of your applications.
KMS with Chef
While the benefits of using KMS are easy to see, it still leaves the challenge of finding a better way to make the encryption process more seamless. We will walk you through the steps you will take to use KMS with Chef.
- Create a new KMS key
- Use KMS to encrypt the desired file or key
- Create a new server with an IAM role to allow access to the KMS key
- Utilize Chef to use the encrypted file in a cookbook
1. Create a new KMS key
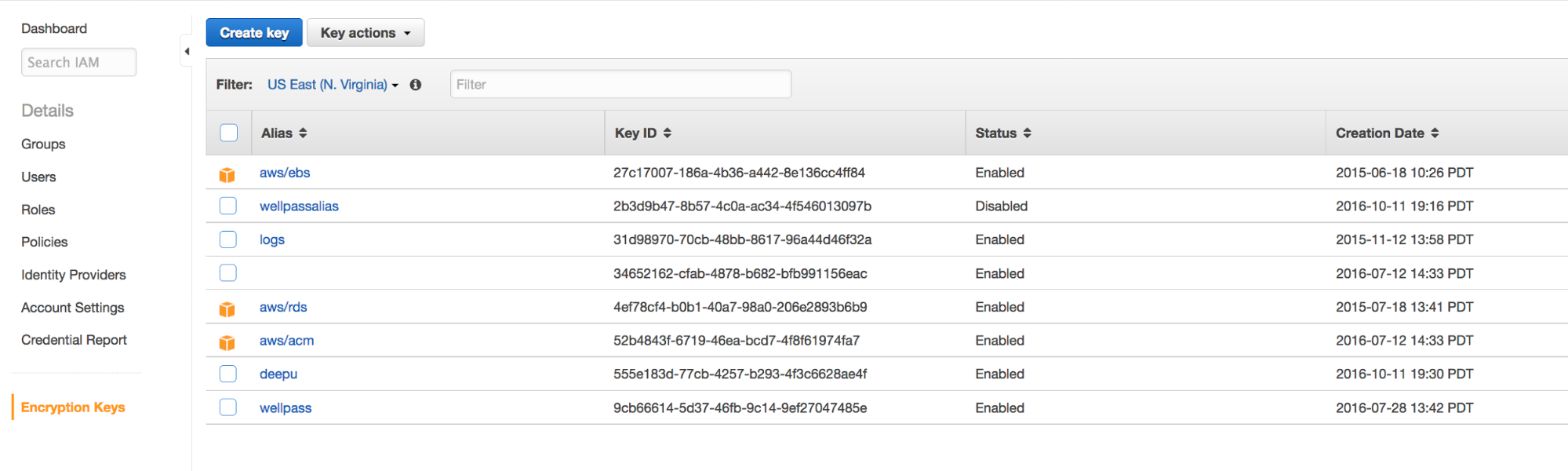
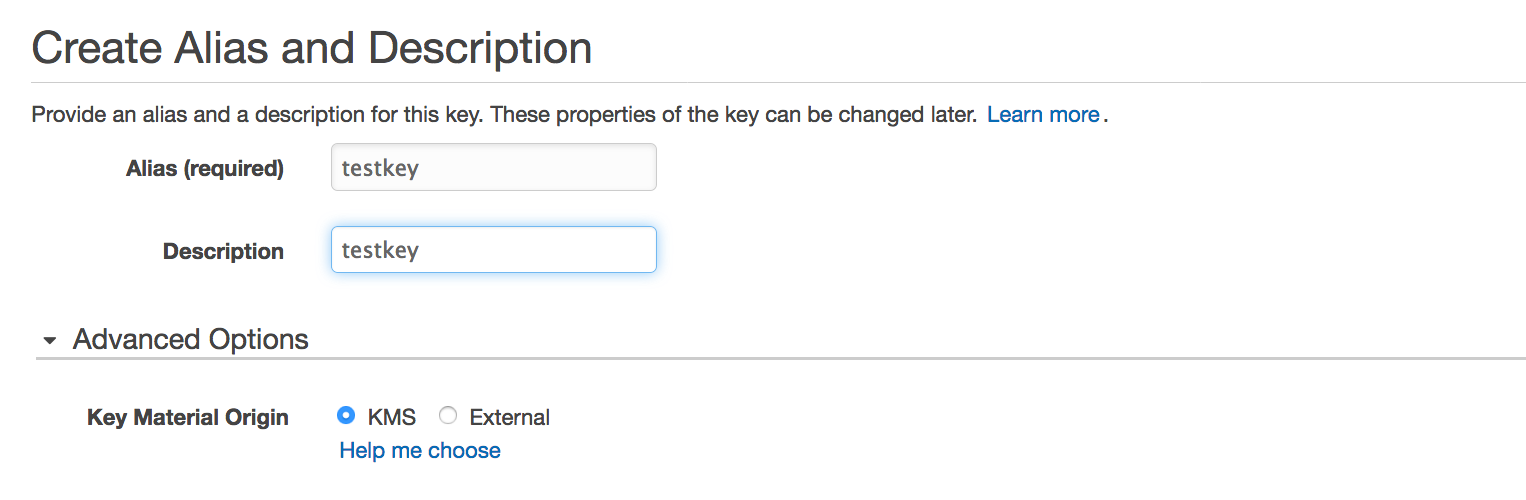
2. Use KMS to encrypt the desired file or key
aws --region us-west-2 kms encrypt --key-id 627ae045-b663-421d-b09a-57f424f13698 --plaintext "abcd" --query CiphertextBlob --output text | base64 --decode > /tmp/encrypted-fileOr
aws --region us-east-1 kms encrypt --key-id 9cb66614-5d37-46fb-9c14-9ef27047485e --plaintext fileb:///tmp/mongodb1.pem --query CiphertextBlob --output text | base64 --decode > /tmp/mongodb.pemHere is the documentation – https://docs.aws.amazon.com/cli/latest/reference/kms/encrypt.html
3. Create a new server with an IAM role to allow access to the KMS key
Make sure the node has right IAM role permission to use the KMS token for decryption later.
Eg Policy
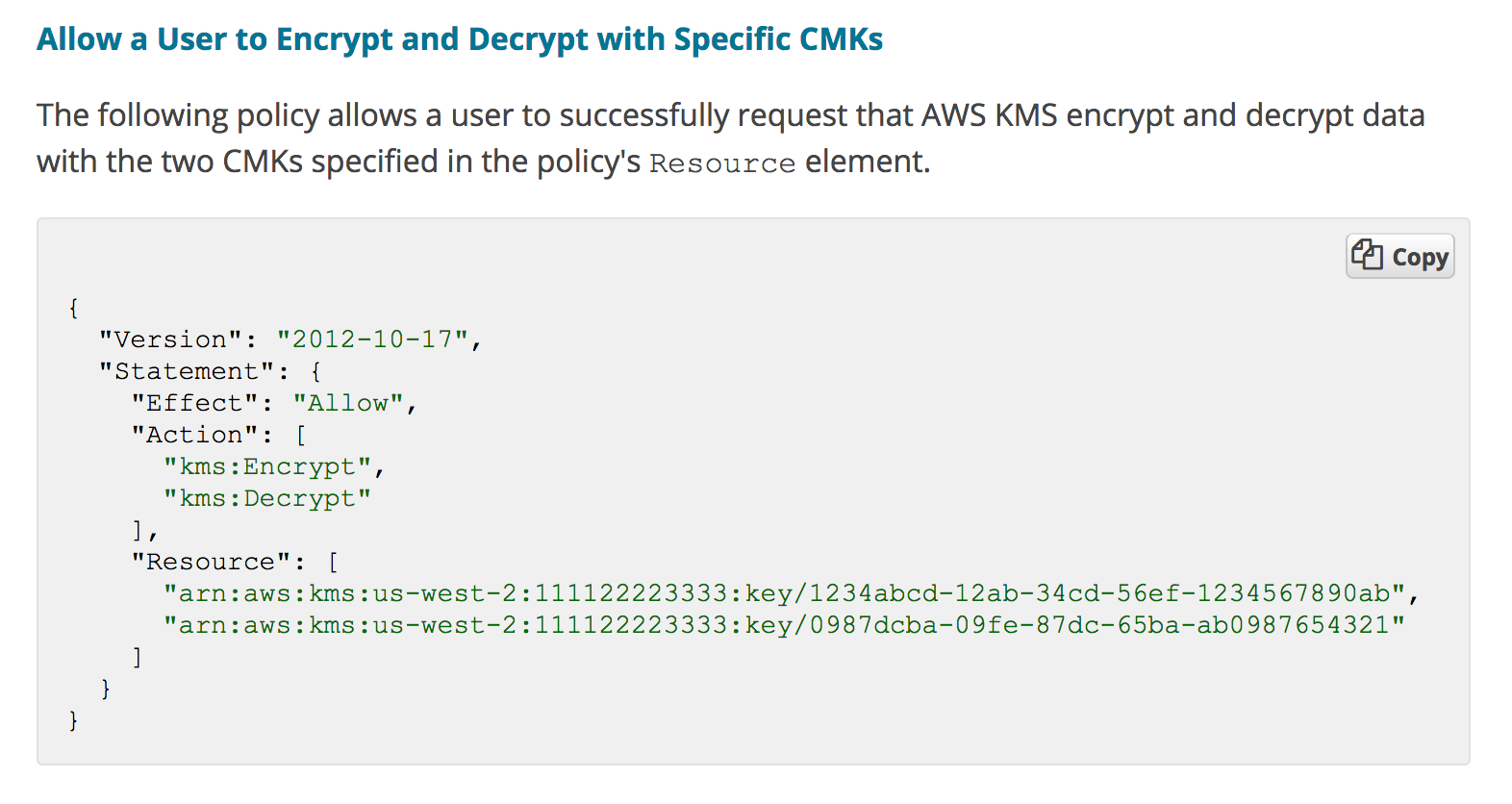
4. Utilize Chef to use the encrypted file in a cookbook
Now lets use Chef to use this encrypted file in a cookbook .
Willejs had an excellent library cookbook which will do the decryption part as a LWRP.
aws-kms cookbook –
This library cookbook gives you a simple workflow for encrypting secrets with AWS kms and then using chef to decrypt and store them on an instance.
More details – https://github.com/willejs/chef-aws-kms
Usage
There is an example .
First encrypt the key and keep under cookbook
cookbook_file "/home/ec2-user/encryptedkey/#{node['mdm_rsynclogs']['key']}.crypt" do
source "keys/#{node.chef_environment}/#{node['mdm_rsynclogs']['key']}.crypt"
owner 'root'
group 'root'
action :create
endUse aws_kms to decrypt the key .
aws_kms 'rsyncprivatekey' do
crypt_folder "/home/ec2-user/encryptedkey"
decrypt_folder "/home/ec2-user/"
action :decrypt
endProperties for aws_kms
- crypt_folder – Where your collection of .crypt folders are stored, this could be in a cookbook, or baked into your ec2 image, or dropped on the box some other way. String.
- manage_crypt_folder – Create and ensure permissions on folder. Boolean
- decrypt_folder – The location to decrypt the files to. String
- manage_decrypt_folder – Create and ensure permissions on folder. Boolean
Following these simple steps, you will be able to easily store and retrieve sensitive data with KMS for use in Chef in no time.


